I haven't seen this come up before in a scan like this, thanks for sharing!
This is due to the compiler, but rather than obfuscation, this is due to the compiler solving for a constant value rather than doing the math at runtime. This same constant appears in the GWT showcase as well, at https://samples.gwtproject.org/samples/Showcase/Showcase.html in the https://samples.gwtproject.org/samples/Showcase/showcase/deferredjs/5F20F7F6874DB82B437E6EA4319E4E9B/47.cache.js file.
function Hmc(a,b,c,d,e,f){Gmc();this.a=e;Th(a,Dwc(b,c,d,e,f));a.db==-1?(Sbc(),Idc(a.hb,133333119|(a.hb.__eventBits||0))):(a.db|=133333119)}
This is slightly different from yours, and not just in the obfuscation - I suspect that you have emulated stack traces enabled, which should allow you to check the value of the NWl and RWk constants to confirm - they should be the "stack trace element" information, like class+method name, line number etc.
In this case, that particular line comes from Image.java's constructor. That calls the constructor of the inner class UnclippedState, which has these lines:
UnclippedState(Image image) {
image.replaceElement(Document.get().createImageElement());
// We are working around an IE race condition that can make the image
// incorrectly cache itself if the load event is assigned at the same time
// as the image is added to the dom.
Event.sinkEvents(image.getElement(), Event.ONLOAD);
// Todo(ecc) this could be more efficient overall.
image.sinkEvents(Event.ONCLICK | Event.ONDBLCLICK | Event.MOUSEEVENTS | Event.ONLOAD
| Event.ONERROR | Event.ONMOUSEWHEEL | Event.TOUCHEVENTS | Event.GESTUREEVENTS);
}
image.replaceElement(Document.get().createImageElement());
// We are working around an IE race condition that can make the image
// incorrectly cache itself if the load event is assigned at the same time
// as the image is added to the dom.
Event.sinkEvents(image.getElement(), Event.ONLOAD);
// Todo(ecc) this could be more efficient overall.
image.sinkEvents(Event.ONCLICK | Event.ONDBLCLICK | Event.MOUSEEVENTS | Event.ONLOAD
| Event.ONERROR | Event.ONMOUSEWHEEL | Event.TOUCHEVENTS | Event.GESTUREEVENTS);
}
That chained | expression results in the number you're seeing. Then, that value is passed to Widget.sinkEvents(), which looks like this:
@Override
public void sinkEvents(int eventBitsToAdd) {
if (isOrWasAttached()) {
super.sinkEvents(eventBitsToAdd);
} else {
eventsToSink |= eventBitsToAdd;
}
}
public void sinkEvents(int eventBitsToAdd) {
if (isOrWasAttached()) {
super.sinkEvents(eventBitsToAdd);
} else {
eventsToSink |= eventBitsToAdd;
}
}
The isOrWasAttached() call is a comparison of a field to -1, and a ternary is used instead of an if/else for this:
a.db==-1 ?
(Sbc(),Idc(a.hb,133333119|(a.hb.__eventBits||0))):
a.db==-1 ?
(Sbc(),Idc(a.hb,133333119|(a.hb.__eventBits||0))):
(a.db|=133333119)
Now it becomes clear that "this.eventsToSink" is "a.db", and "eventBitsToAdd" is the constant int 133333119.
Links to github source to confirm:
https://github.com/gwtproject/gwt/blob/1671fc2730e23b371962f482830c090b901ea54e/user/src/com/google/gwt/user/client/ui/Image.java#L371-L381
https://github.com/gwtproject/gwt/blob/1671fc2730e23b371962f482830c090b901ea54e/user/src/com/google/gwt/user/client/ui/Widget.java#L238-L245
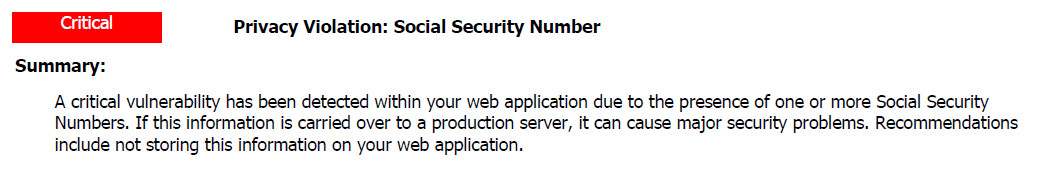
So - this is not a SSN, but just happens to have the same number of digits.
On Tuesday, April 11, 2023 at 1:35:58 PM UTC-5 cyclop...@gmail.com wrote:
We hava a GWT project, and user use WebInspect to scan, then they found a critial issue as below in the file 30.cache.jsWhat's the "133333119" ?Is that bacause GWT obfuscate ?Sorry we don't have the source codes of this GWT project (We just have WAR file only)Many thx.
You received this message because you are subscribed to the Google Groups "GWT Users" group.
To unsubscribe from this group and stop receiving emails from it, send an email to google-web-toolkit+unsubscribe@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/google-web-toolkit/562db861-68c1-43d8-81fa-65ac79d00681n%40googlegroups.com.

No comments:
Post a Comment